In today’s industrial world, data is king - but only if it’s accessible, accurate, and connected. Unfortunately, many organizations face a sneaky intruder: the Data Grinch. Unlike its Christmas counterpart, this troublemaker isn’t after gifts or holiday cheer. It steals efficiency, insights, and the very momentum of your digital transformation. It hides in siloed systems, outdated protocols, scattered data, and fragile integrations. Left unchecked, it slows decision-making, frustrates teams, and undermines operational performance.
The Problem: Disconnected Data in a Connected World
Industrial operations have grown increasingly complex. Mergers, expansions, and legacy systems create fragmented data silos where operational data remains trapped in SCADA systems, PLCs, or plant historians. Teams often duplicate data to compensate, creating inconsistencies and extra work. Third-party access adds another headache - VPNs, firewall exceptions, and insecure inbound connections increase risk and make compliance tougher. Legacy protocols, unsupported devices, and point-to-point integrations compound the chaos.
This is exactly where the Data Grinch thrives: in complexity, in isolation, and in the gaps between your systems. The result? This Efficiency Thief is free to snatch the value from your data while you struggle to keep up.
The Solution: A Vendor-Neutral, Standards-Based Data Architecture
The way to keep this mean character at bay is a unified, scalable, and secure data platform. By creating a middleware layer that aggregates, translates, and brokers data across OT and IT systems, organizations can unlock the value of their operational information - without ripping out existing infrastructure.

This empowers operations, analytics, and IT teams to access real-time, reliable data, making collaboration and decision-making faster and smarter. With this foundation in place, teams gain reliable, real-time access to the data that drives performance, innovation, and competitive advantage.
This Is How It Works
A layered deployment ensures both security and flexibility. At the edge layer, data is collected from sensors, controllers, and legacy systems, capturing every piece of operational information at its source. This data then moves to the on-premises aggregation layer, where protocols are translated, data is validated, and local redundancy is provided to maintain continuous operations. From there, the DMZ or data hub layer aggregates and brokers the information, normalizes data structures, and enforces access controls, ensuring that only authorized users and systems can access the right data. Finally, the IT and cloud layer securely feeds analytics platforms, dashboards, and third-party applications, delivering insights where they are needed most. All data flows are encrypted, outbound-only, and role-controlled, keeping the efficiency thieves out of your OT systems while preserving visibility and control.
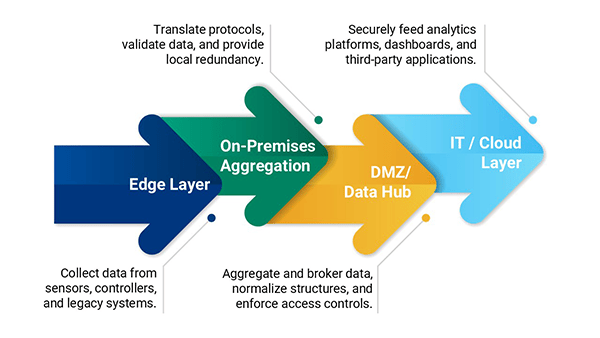
All flows are encrypted, outbound-only, and role-controlled - keeping the Data Grinch out of your OT systems.
Real-World Impact
A multi-site industrial operator recently deployed a standards-based integration layer with transformative results. By unifying data across multiple departments, the organization enabled both site-level monitoring and corporate analytics, breaking down long-standing silos. External partners were granted secure, role-based access to selected datasets without opening risky inbound ports, strengthening cybersecurity posture. The architecture-maintained continuity with redundant aggregation nodes, ensuring operations continued smoothly even if a node went offline. Starting with a pilot plant, the deployment scaled to enterprise-wide adoption without the need to reengineer the architecture. The outcome was clear: faster insights, safer collaboration, and a digital transformation that actually delivers tangible business value.
One multi-site industrial operator deployed a standards-based integration layer:
 The result? Faster insights, safer collaboration, and a digital transformation that actually delivers.
The result? Faster insights, safer collaboration, and a digital transformation that actually delivers.
Best Practices to Keep the Efficiency Thieves Away
Protecting your data starts with a thorough audit of your current systems, mapping data flows, identifying gaps, and understanding potential risks. Next, define clear integration goals that align with operational, IT, and security objectives, ensuring all stakeholders are engaged in the process. Start small by piloting the integration architecture at a single facility, validate performance, and then scale incrementally to other sites. Empower OT teams to manage the integration directly, reducing dependence on scarce IT resources and enabling faster, more responsive implementation. Finally, secure collaboration is essential—use role-based access controls and outbound-only tunnels to safely share data with third-party partners while protecting sensitive operational systems. 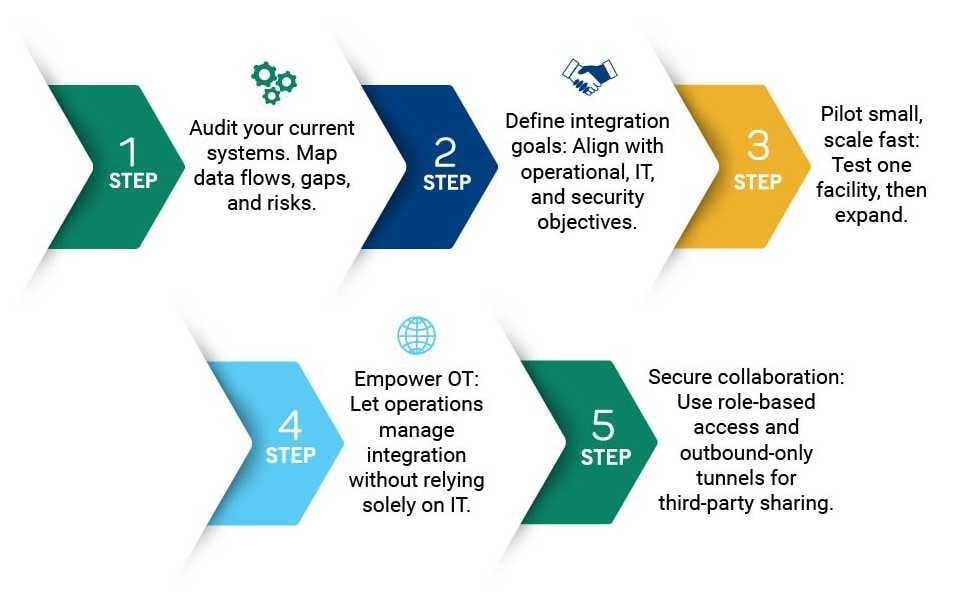
Take the First Step
The Data Grinch thrives where data is fragmented, insecure, or inaccessible. By implementing a vendor-neutral, secure, and scalable architecture, organizations can centralize, govern, and unlock their industrial data—turning a potential villain into a competitive advantage. Don’t let disconnected systems, legacy protocols, or risky integrations steal your transformation. Give your data the gift of unity this season.
If you’d like guidance tailoring these strategies to your environment, schedule a consultation with our subject matter experts. We’re here to help you move forward with clarity and momentum.






