A common use case that we encounter with many AVEVA™ users is the need to share data from System Platform with some other client or system (HMI, SCADA, other). It's not uncommon for a company to be acquired by another company and its assets and a non-AVEVA HMI/SCADA came as part of the assets. Or perhaps a system is being add with limited interfaces for external connectivity. Your options for sharing data largely depend on what software interfaces these "other systems" support.
In this blog post, I'll discuss how to share your AVEVA System Platform 2020 (or newer) data via OPC UA (without using OI Gateway) using the OPC Router for situations where you have another non-OPC UA capable client application that needs access to process data in your AVEVA system such as an ERP system, IIoT platform, web service and more.
As you may be aware, starting with AVEVA System Platform 2020, a native OPC UA server interface is available. So, of course, if the other system that needs to access data from System Platform can act as an OPC UA client, you can connect it directly to System Platform. However, if the other system cannot act as an OPC UA client, you'll need another method.
Using an older version of System Platform? Click Here for Our Other How-To
Now, you could certainly use the OI Gateway to expose the System Platform data externally but you're limited to the other interfaces that OI Gateway supports (such as OPC DA or SuiteLink). However, for users looking for alternatives or needing to connect a system via an interface that isn't supported by OI Gateway, the OPC Router makes it possible to convert data from OPC UA servers like System Platform 2020 or newer to other supported interfaces, including but not limited to a wide range of databases (SQL, of course, but also MariaDB, Mongo DB, and more), OPC DA servers, other OPC UA servers, MQTT brokers, SOAP and REST web services, ERP systems including SAP and more.
With its visual workflow configuration, OPC Router makes it possible to easily setup the flow of data from one interface to another for any of it's supported interfaces.
To make an OPC UA Client connection to AVEVA System Platform, there are 3 main steps:
1. Configure the OPC UA Server Interface in AVEVA System Platform 2020 or Newer
The first step is creating and configuring an instance of the OPC UA Service in your System Platform ArchestrA IDE that will be accessible with the desired Port and security settings for external OPC UA client applications. So we need to do the following:
- Inside the ArchestrA IDE, in the menu bar at the top we select Galaxy -> Configure -> ArchestrA Services.
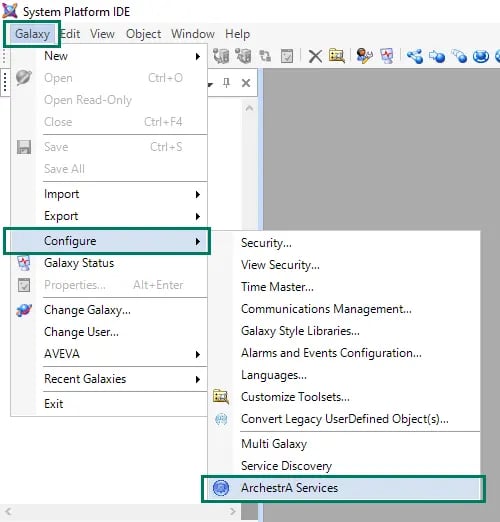
- This launches the "Configure ArchestrA Services" dialog where we need to expand the IDE name.
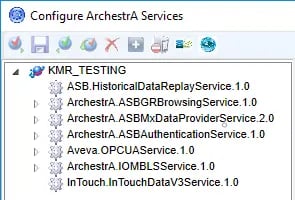
- Next, we find "Aveva.OPCUAService.[Version]" in the list, right-click and select "Create" to create a new instance of the OPC UA Service (if you have a default instance already created that you wish to use, you can skip this step).
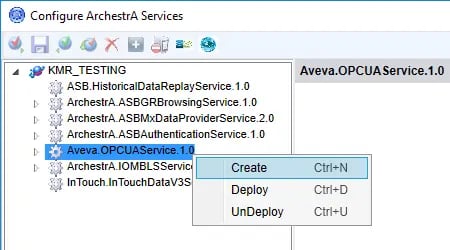
- Expanding "Aveva.OPCUAService.[Version]" in the tree hierarchy shows the new instance with the default name of "OPCUAService_001" - to edit this, we need to right-click on the new instance and select "Check-out" to permit us to make the required changes.
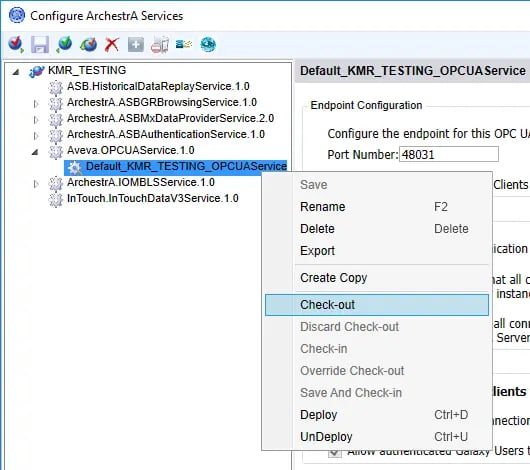
- It's now possible to make edits to the following properties of the OPC UA Service instance in the right-hand pane of "Configure ArchestrA Services".
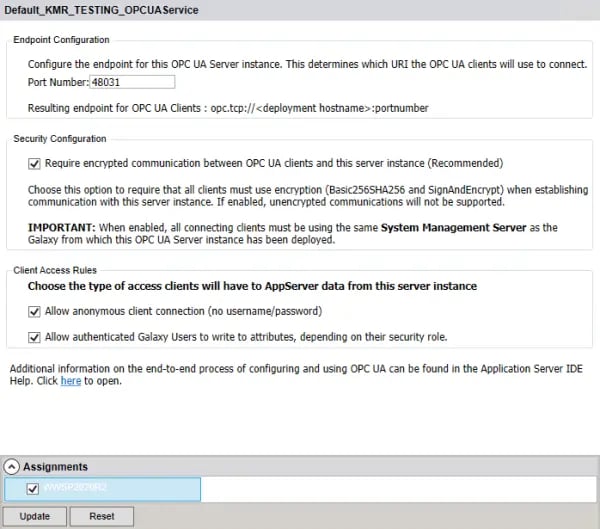
- Port Number - this defines the port portion of the endpoint that OPC UA clients will need to use to access this OPC UA server instance (as well as, the port that will need to be allowed in any firewalls between the OPC UA client and server machines). The default is 48031. Consult your IT department for the best port to specify for your particular application.
- Require encrypted communication between OPC UA clients and this server instance - By default, this setting is enabled, requiring that all OPC UA clients that want to connect to this OPC UA server instance must be using encryption (System Platform currently supports Basic256SHA256 with SignAndEncrypt - so the OPC UA client needs to use the same exact level of encryption).
Disabling this setting, which is not recommended, will allow OPC UA clients to connect without using any encryption, lowering the security level on your System Platform IDE and adding risk from outside security threats. This is especially true for applications where you plan to allow OPC UA clients to write to your IDE. Consult your IT department to discuss the risks of disabling this setting on your network. - Allow anonymous client connection (no username/password) - Leaving this setting enabled will allow any OPC UA client to connect to this OPC UA server instance without specifying an approved username and password. This is not recommended, as it removes an additional layer of security.
- Allow authenticated Galaxy Users to write attributes, depending on their security role - Leaving this setting enabled will allow IDE/Galaxy users that have provided a valid username/password when connecting to this OPC UA server instance and that user has the appropriate security role for changing attributes to perform writes. Disabling this setting will essentially make all OPC UA connections to this server instance read-only regardless of the authentication used.
- Assignments - Deployment hosts that are available for deploying this OPC UA Server instance will be available to select here. Depending on what host you select, the Assignment plus the previously defined Port Number will determine the OPC UA Endpoint URL that an OPC UA client will need to use to connect.
For example, if the hostname is "WWSP2020R2" with the default Port of 48031, then the OPC UA Endpoint URL will be:
opc.tcp://WWSP2020R2:48031
- Port Number - this defines the port portion of the endpoint that OPC UA clients will need to use to access this OPC UA server instance (as well as, the port that will need to be allowed in any firewalls between the OPC UA client and server machines). The default is 48031. Consult your IT department for the best port to specify for your particular application.
- Once the above settings have been configured as desired or required for your application, we click the "Update" button to apply any changes.
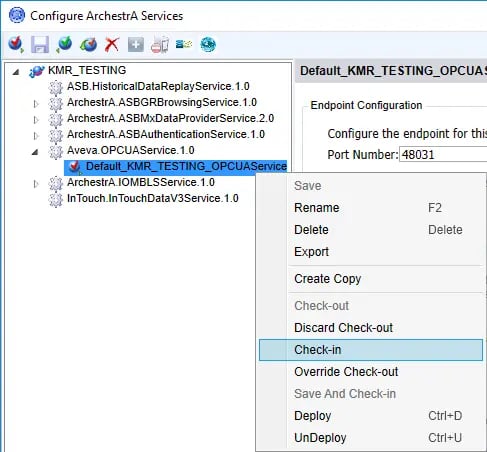
- Next, we need to right-click on the instance again in the tree hierarchy and select "Check-In" to check the instance back in after the edits have been applied.
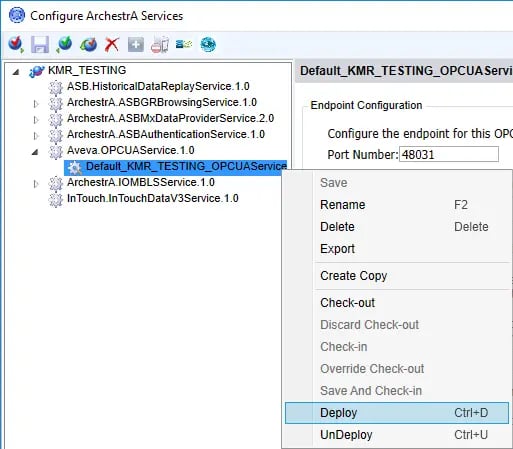
- And last but not least, we need to deploy the new OPC UA server instance by right-clicking on the instance again and selecting "Deploy". This pushes the service to the selected Assignment node where it will begin running and be available to OPC UA clients.
- We can now go ahead and close out of the "Configure ArchestrA Services" dialog window, as configuration on the OPC UA server side is complete for now (we'll revisit trusting the OPC UA client certificate after the initial OPC UA client connection attempt from OPC Router).
NOTE: Depending on how your IT department has security configured on both the client and server machines, it may be necessary to request a firewall exception for the TCP port you specify for the OPC UA server. Please consult your IT department.
2. Configure OPC Router as an OPC UA Client Connecting to AVEVA System Platform
Now that the OPC UA server service for System Platform has been configured and deployed, the next step is configuring OPC Router to act as an OPC UA client to that server with the following configuration:
-
We first need to go to the Plug-Ins section of the OPC Router configuration and double-click on OPC UA under the Shopfloor section, then click the Add Instance button.
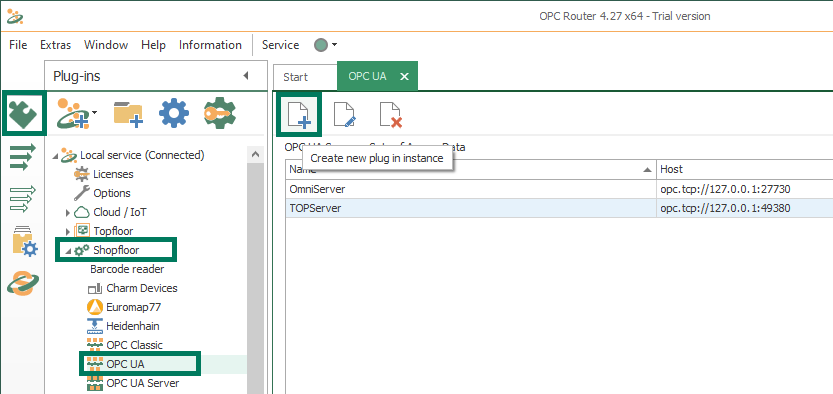
- This allows us to add a new connection to the OPC UA server in System Platform by specifying the following available settings (we'll cover just the key settings that need to be configured to connect with System Platform - all other settings can be left at the defaults):
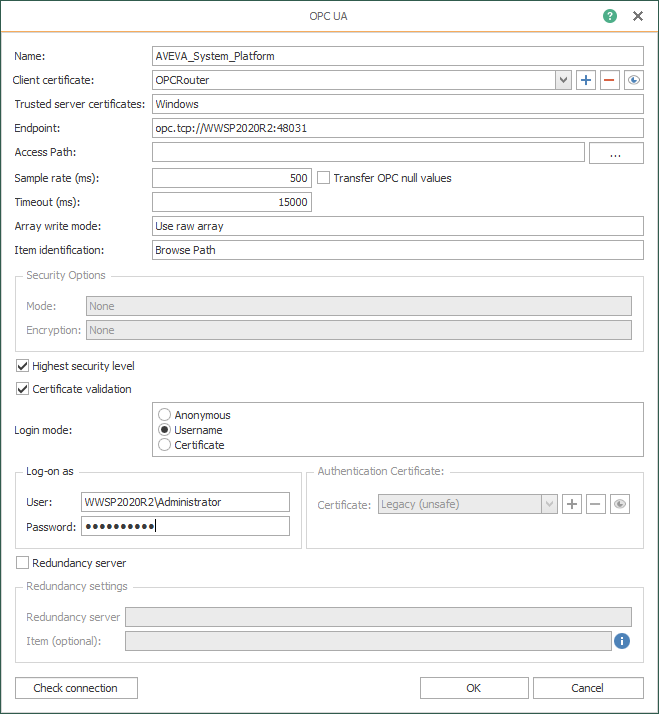
-
Name - User-defined friendly name used by OPC Router to identify this connection.
-
Client Certificate - Selects which certificate the OPC Router OPC UA Client will use for encrypting this connection. It is recommended to create a new certificate here by clicking the blue "+" button, which brings up the following "Create certificate" dialog. Keep the defaults on everything but the expiration period (the default is 120 months or 10 years - choose a period that works for your application with the understanding that the certificate will need to be reissued and exchanged with the server again after that period).
Click Create to complete the certificate, which will be selected automatically.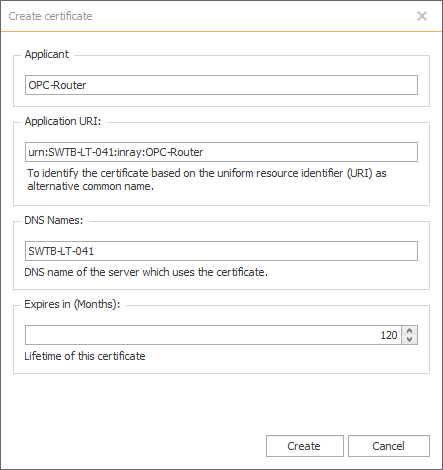
- Trusted server certificates - Selects which OPC UA server security certificates to accept/trust. The default setting is "All" which will result in the certificate of the OPC UA server being connected to getting trusted automatically. It is recommended to select "Router" here, which will prompt us to either trust or reject the server's certificate when attempting to connect, allowing us to review the certificate before trusting it.
- Endpoint - Here we can enter the full URL referenced in the properties of the OPC UA Service instance in System Platform that we saw earlier including the opc.tcp:// prefix and following by the port.
- Security Options - By default, "Highest security level" is enabled which results in OPC Router using the highest level of security that both OPC Router and the OPC UA server both support. Currently, the highest level of security is the same as System Platform: Basic256Sha256 with Sign&Encrypt so we're fine to leave this enabled.
If you're unsure, you can disable "Highest security level" and manually select the Mode and Encryption levels that correspond to what the OPC UA server supports (as these levels are subject to change over time as higher levels of encryption support is added). For the connection to System Platform, we need to select Basic256Sha256. - Login Mode - For authentication, OPC Router defaults to Anonymous. To perform writes or if anonymous connections in the OPC UA settings in System Platform have been disabled, this where the "User" and "Password" for the System Platform galaxy need to be entered.
- Check Connection - This button allows you to confirm that your connection settings are correct. But with OPC UA, there are some additional steps required before the test will complete successfully due to the require certificate exchange for encrypted OPC UA connections. So, first, we need to click the button:
- We get the following warning, since we have not yet trusted System Platform's security certificate for encryption - we can do so by simply clicking "Yes" (we could also review the certificate first by clicking "Show certificate".
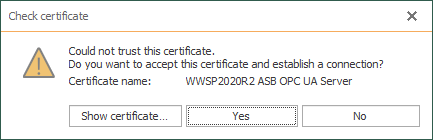
- However, the first attempt will still fail due to OPC Router's certificate not yet being trusted by System Platform. So prior to being able to successfully connect and then browse and select items we want to access from System Platform, we need to establish that trust relationship.
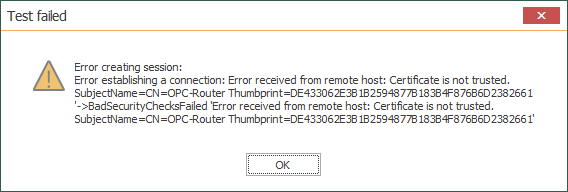
- On the System Platform galaxy machine, we need to browse to C:\ProgramData\AVEVA\PCS\OPC UA Rejected Client Certificates\certs where we find the .der certificate for OPC Router.
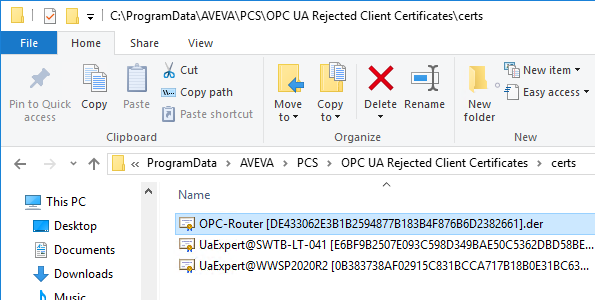
- Next we need to install the certificate so that it will be trusted. To do this, we need to right-click on the .der file and select "Install".
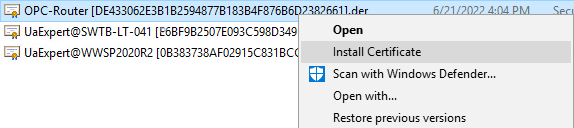
- This launches the Certificate Import Wizard. We need to select "Local Machine" for the Store Location and click Next.
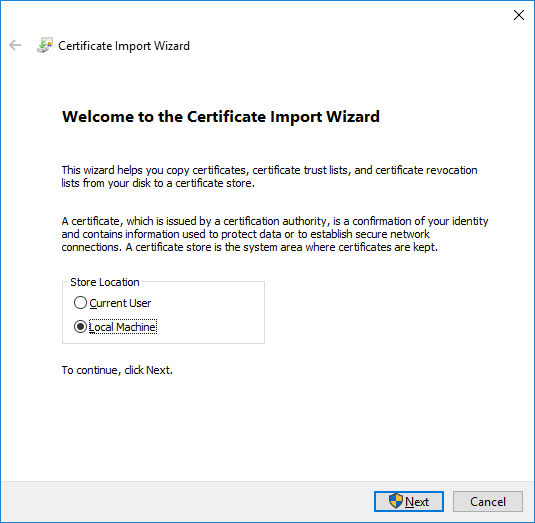
- Now we select "Place all certificates in the following store", click Browse and select "Trusted People" from the list, then click Next.
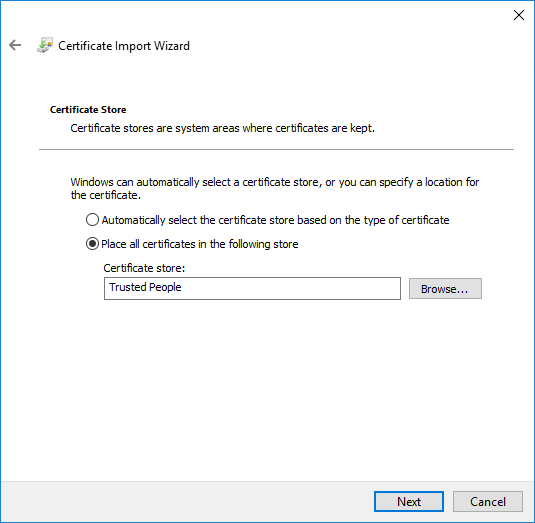
- Confirm the settings are correct and click Finish.
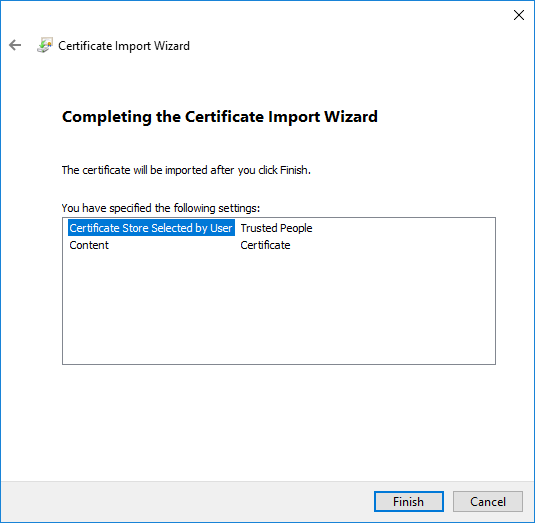
- Then you'll get a confirmation that the certificate was successfully imported.
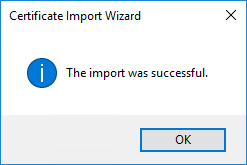
- Now, back in the OPC Router, you can click the Check Connection button again and it will now complete successfully. Now we can proceed and configure the Nodes (i.e. items or tags) we'd like to access in System Platform.
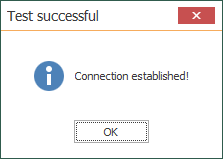
- We get the following warning, since we have not yet trusted System Platform's security certificate for encryption - we can do so by simply clicking "Yes" (we could also review the certificate first by clicking "Show certificate".
- Now that all of the connection settings are complete, we can click OK to complete this part of the configuration.
-
- The next step is using this new OPC UA connection for data transfer in a visual workflow template in OPC Router. Given the wide variety of options available for the full workflow, we'll just step through the OPC UA source part of the configuration specific to System Platform for the purposes of this post.
Then I'll refer you to some specific how-to tutorials for full workflow scenarios that would allow you to transfer data from System Platform to text files or SAP or other systems by simply using your OPC UA connection to System Platform as the source in the workflow.
- So we go to the Connections section of the OPC Router Configuration, right-click on Connections (under "Local service") and select "New Connection" from the menu.
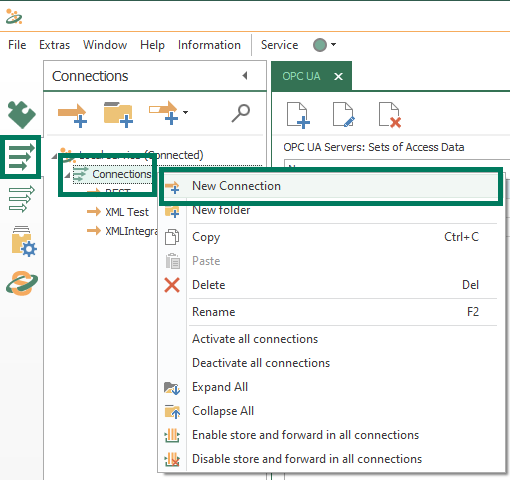
- Enter a representative name for this connection and hit Enter (you can rename the connection at any time by right-clicking on the connection and selecting "Rename").
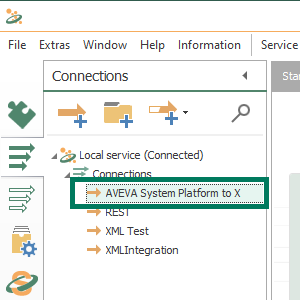
- This opens the new connection. To use OPC UA nodes/items from AVEVA System Platform as a source in OPC Router, we need the OPC Data Access Transfer Object available to the right under OPC Transfer Objects in the "Data Sources and Destinations" section.

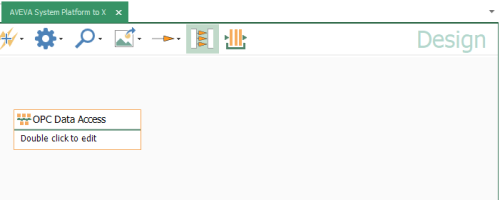
- We need to drag-and-drop and instance of the OPC Data Access object into the design template (we can place it anywhere visually - it can be moved later, as needed).
- Double-clicking the OPC Data Access object opens its properties, where we can select the OPC UA server we just configured from the "OPC access data" dropdown menu at the top.
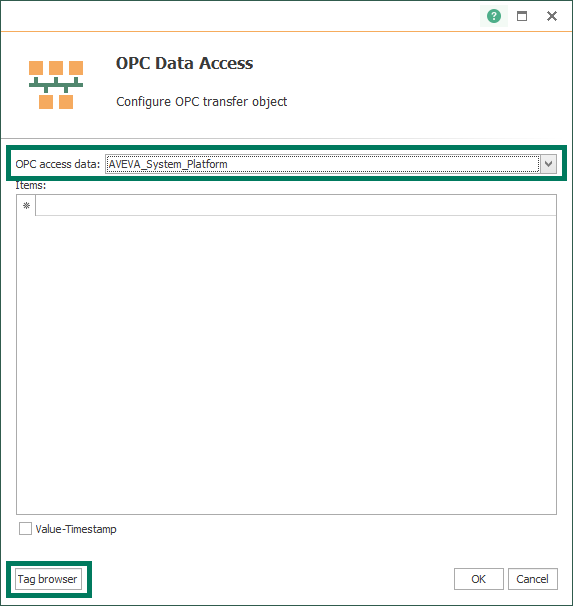
- Now we can click the "Tag Browser" button at the bottom left to select the nodes/items we want to access from System Platform under the Model view section (simply tick the box next to each branch or specific node/item) and then click the center "übernehmen" button to apply the settings.
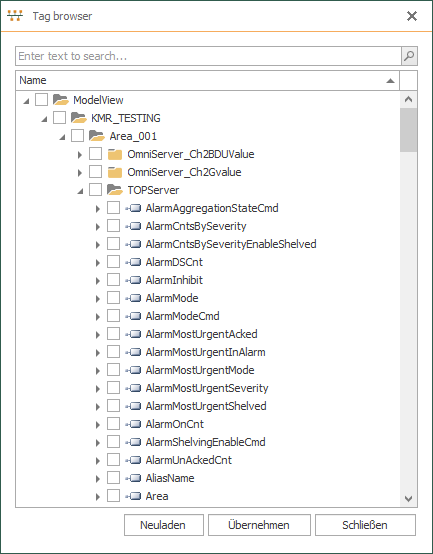
- This adds the selected items to our OPC Data Access object where we can click OK to apply.
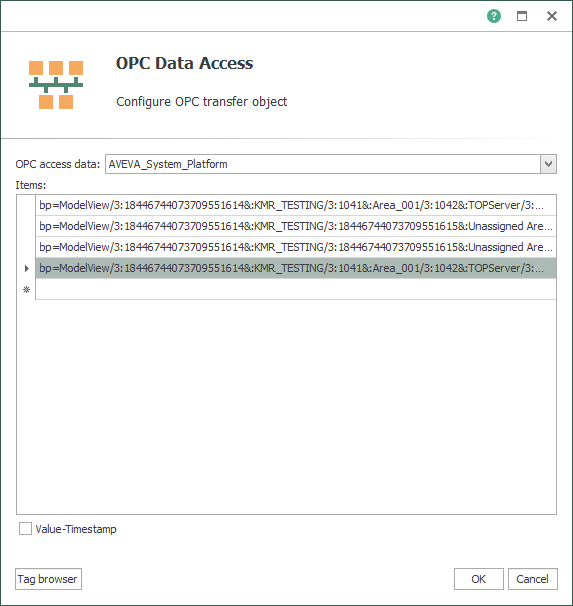
- This object is now ready to use as the source for transfer to any other supported interface/destination supported by OPC Router.
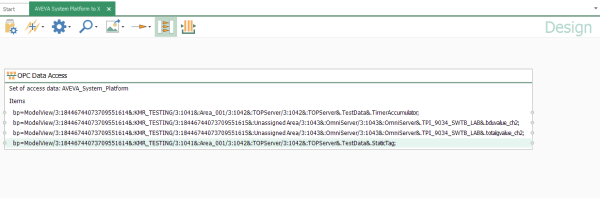
- So we go to the Connections section of the OPC Router Configuration, right-click on Connections (under "Local service") and select "New Connection" from the menu.
3. Configure One of the Other OPC Router Interfaces to Use the Data Points from AVEVA System Platform
Since the ultimate goal of this exercise is sharing System Platform data with other non-OPC UA systems, it would be necessary to also define what the destination is of that data, so that it might be used in a visual workflow. In similar fashion to how we configured the connection to System Platform's UA server, the appropriate Plug-in for the destination system would need to be configured, which is beyond the scope of this post given the wide variety of different plug-ins available in OPC Router.
4. Configure A Visual Workflow in OPC Router to Move System Platform Data to Your Other System
At that point, the plug-in for the data destination can be referenced by the corresponding transfer object (for instance, to use a configured instance of the SAP Systems plug-in, there is an SAP Objects group of transfer objects) in the workflow and connected with the AVEVA System Platform transfer object using Connection Arrows.
For example, if I wanted to log my data values to a text file on a set time interval, I might have a workflow similar to the following (for a how-to video of this use case, click here):
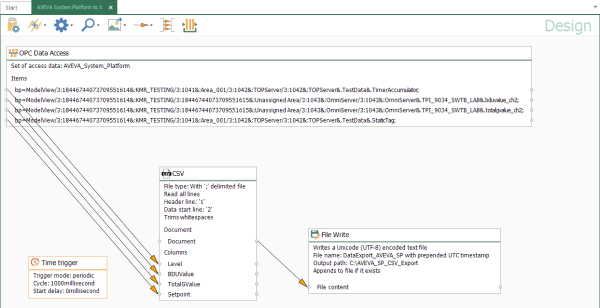
And with all changes in OPC Router, when you're ready to set the configuration active and start communicating, make sure to go to the "Go Productive" section of the configuration and select the elements being used in your project and click the "Go productive" button to publish the changes.
For a wide selection of how-to resources for the other connectivity interfaces in OPC Router, visit our OPC Router videos resources repository for free on-demand tutorials. When paired with the information from this post, you'll be able to get your AVEVA System Platform data shared with a variety of systems including SAP, RESTful web services, databases and more. Try it for yourself with our fully functional free trial of OPC Router.





