If you've been following our ongoing Exploring OPC UA blog series, we've been covering key Software Toolbox solutions and the specifics of configuring OPC UA security and connectivity.
In this eighth post of the series, we will focus on the OPC Data Client development toolkit, with the primary topic being how to exchange security certificates and establish a trust relationship between your custom OPC UA client and an OPC UA server.
OPC Data Client is a rapid development toolkit for quickly adding OPC client connectivity to custom applications including OPC UA and OPC Classic (DA, AE and XML-DA). The OPC Data Client is regularly tested at the OPC Foundation's OPC Interoperability Workshops and has passed their independent lab testing process, ensuring applications developed using OPC Data Client are compatible with OPC compliant solutions.

Among the many benefits of using OPC UA is the focus on security. Not only can the traffic be encrypted, but both the client and server endpoints can be forced to identify themselves (using TLS/SSL certificates), thereby preventing unauthorized client applications and/or machines from connecting to an OPC UA Server. This post focuses primarily on how to properly exchange and trust security certificates between OPC Data Client and the OPC UA server it will be connecting to.
OPC UA Configuration in OPC Data Client
While this post will go into the most detail on certificate exchange (since much of the other OPC UA configuration can be different depending on how the developer implements OPC Data Client in the custom application), we will briefly discuss how OPC Data Client and the methods it exposes for handling OPC UA Server endpoints, encryption and user authentication.
1. OPC UA Server Endpoints in OPC Data Client
An OPC UA Server Endpoint is a physical address available on a network that allows clients to access one or more services provided by a server. Server endpoint is specified by its URL string. For those more familiar with OPC DA Classic, the UA server endpoint is similar to an OPC DA Server ProgID.
OPC Data Client uses an OPC UA Endpoint Selection Policy that allows you to specify flexible criteria that OPC Data Client will use when picking up the endpoint from those made available by the target OPC UA server. The goal of this policy is to make client applications written with OPC Data Client as flexible as possible with respect to successful connections now and in the future, when the details for the server may have changed. For instance, this could happen if the currently selected encryption algorithm became outdated and the UA server stopped supporting it.
The developer might choose to expose fields for the user to define the endpoint and encryption to be used for a connection in a user interface or not - so how those settings are configured are really specific to how the developer implement OPC Data Client in the custom application.
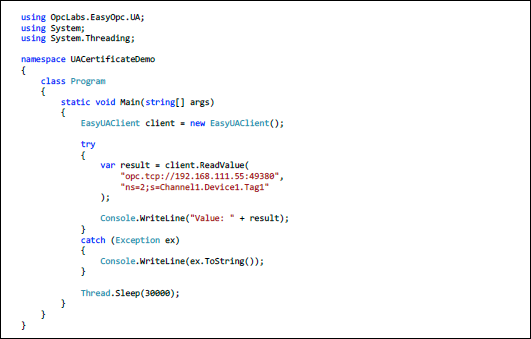
2. OPC UA Authentication in OPC Data Client
In addition to encryption, an OPC UA connection with either be anonymous (not recommended for secure applications) or will require authentication between the UA client and server. OPC Data Client supports user authentications via username/password (most common), Kerberos token, security certificate or anonymous connections.
OPC Data Client provides extension methods that are part of the class for defining OPC UA endpoints that allow developers to handle authentication.
3. Exchanging OPC UA Security Certificates in OPC Data Client
For the a custom OPC Data Client application to successfully connect to an OPC UA server that requires encryption (which is recommended for secure communications), it is necessary to exchange and trust security certificates with the OPC UA server.
- Exporting and Exchanging OPC Data Client certificate with OPC UA server
This can be accomplished most easily by attempting to make a connection from your client application to the underlying OPC UA server. You'll receive a notification similar to the following.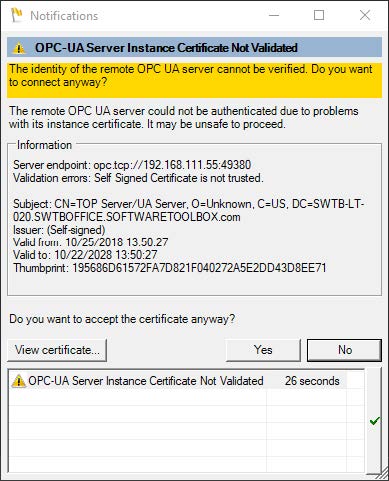
This indicates that the OPC UA server certificate is not trusted and prompts the user to choose whether the server certificate should be trusted. Selecting "No" will reject the OPC UA server certificate and the application will throw an exception.
In order to trust the certificate and continue with the connection process, the certificate must be trusted with the "Yes" button. The selection here is not persisted between runs; this means the next time the app is launched this prompt will be presented again.
Now, even though the server certificate has been trusted by the client, an exception is thrown to the console (specifically a "BadSecurityChecksFailed" error). This is expected, at this point, given that the OPC UA server does not yet trust the client.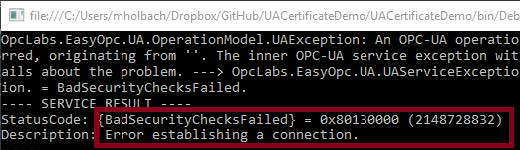
- Exporting and Exchanging OPC UA server certificate with OPC Data Client
In most OPC UA servers, a failed connection attempt by an OPC UA server will result in the client's certificate being listed in the UA server in it's OPC UA configuration settings as "untrusted", "rejected" or some other similar designation. So, after that initial failed connection, establishing that trust is as simple as finding that section in your OPC UA server and changing that designation to be trusted.
For example, see below how TOP Server handles OPC UA client requests prior to trust and how you can simply highlight the client's certificate (1) and click the "Trust" button (2).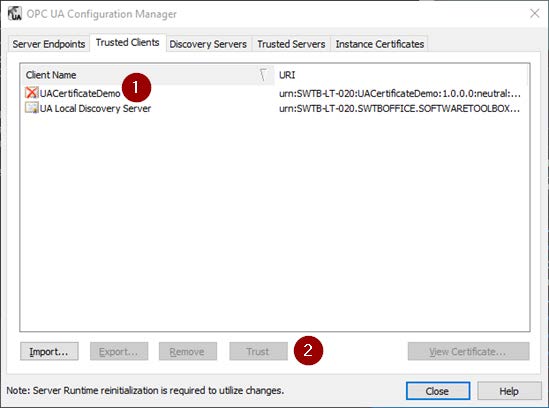
You'll need to consult the help documentation for your OPC UA server to determine specifically how to import and trust client certificates (since this varies between OPC UA servers). - Exchanging OPC UA certificates manually
Now if you're working with an OPC UA server where the OPC UA client certificate does not automatically appear in a "rejected" state as described above, the certificate will need to be manually imported into the server’s trusted client certificate list.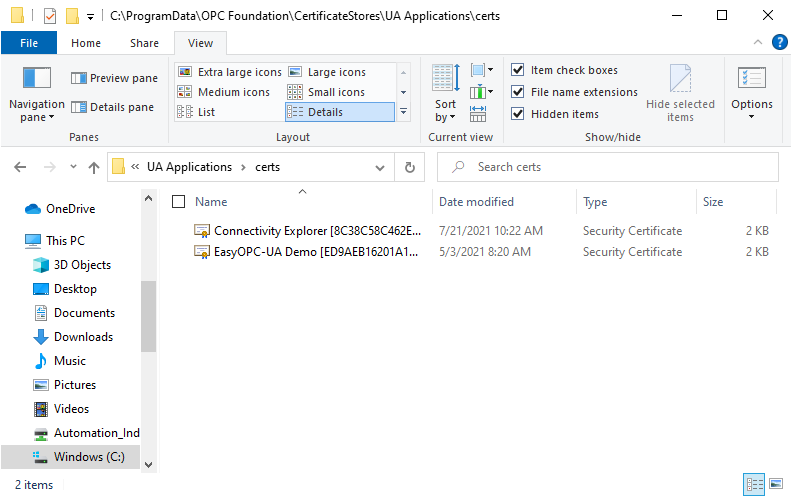
The OPC Data Client’s OPC UA Client certificate can be found by default at:
%CommonApplicationData%\OPC Foundation\CertificateStores\UA Applications\certs
The %CommonApplicationData% directory is most commonly located at C:\ProgramData\ on most systems. Steps to import the certificate into an OPC UA server manually will vary based on the OPC UA Server in use. As mentioned above, you'll need to consult your OPC UA server’s documentation for instructions since some servers provide a means to import certificates in the user interface and others require you to simply copy the certificate file into a specific directory.
And to manually trust your OPC UA server's certificate, consult the server's documentation on either how to manually export its certificate or where the certificate is located and copy the certificate the same directory where your OPC Data Client certificate is located (as shown above).
Get Started Building a Custom OPC UA Client
For a walkthrough detailing how to build no code and low code OPC UA client applications with OPC Data Client, I encourage you to watch the detailed how-to video here. The detailed on-demand training covers how to build a basic OPC UA client and get connected to an OPC UA server. And, you can try out everything as you follow along with the free trial of OPC Data Client.
Subscribe to our blog to stay tuned for the rest of this series where we will continue looking at how to specifically secure more OPC UA solutions available from Software Toolbox, which should be useful to our users migrating to OPC UA but uncertain of how to take full advantage of the security benefits.





