As Cogent DataHub continues to evolve, version 11.04 delivers a focused set of enhancements that build on the powerful foundation introduced with the V11 major release. This update prioritizes performance, reliability, and expanded cloud readiness, ensuring DataHub remains a trusted platform for moving industrial data efficiently and securely.
Software Toolbox Technical Blog
NEW Release - DataHub V11.0.4
7 min read
By Jessica Dillon on Jan 22, 2026 4:00:00 PM
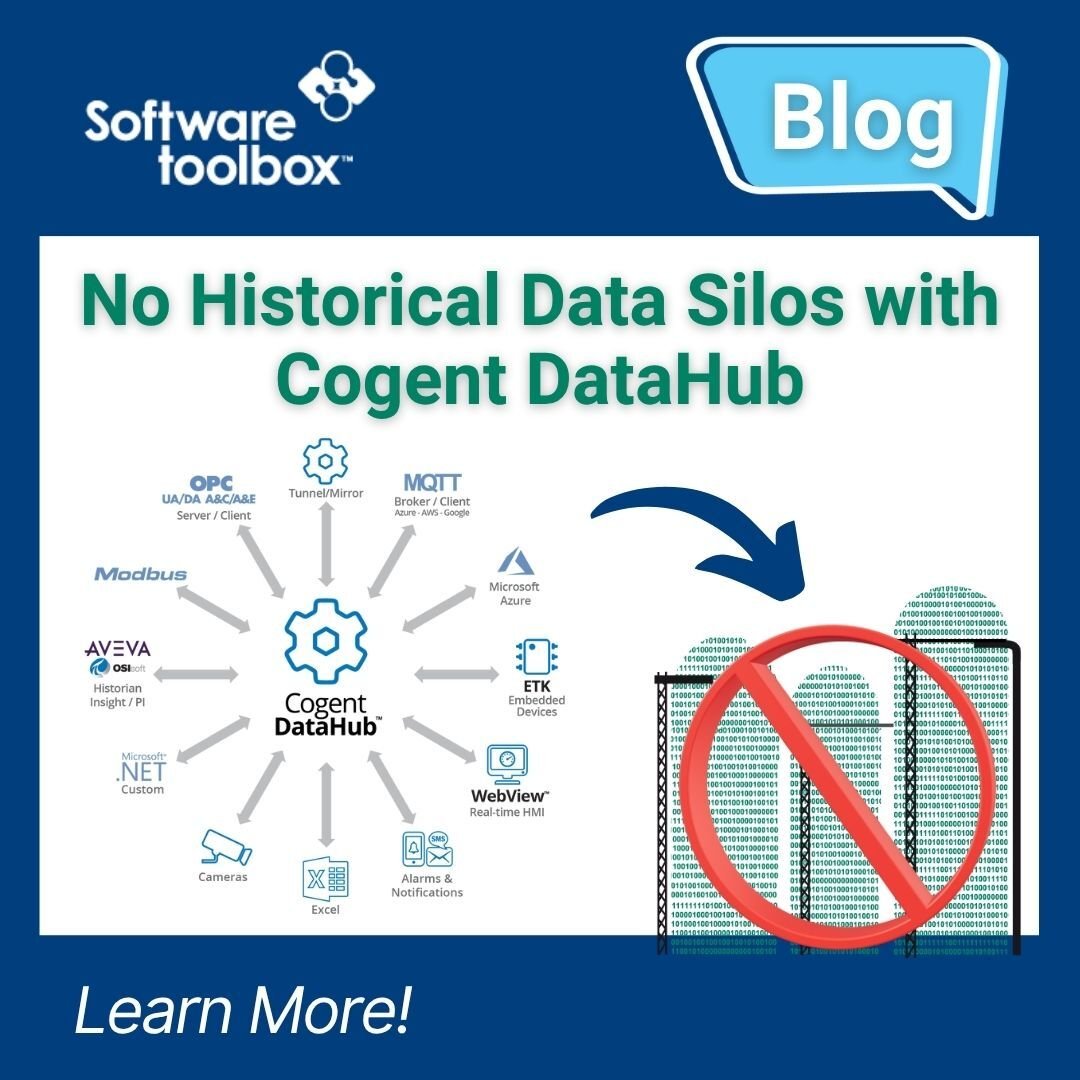
Breaking down Historical Data Silos with Cogent DataHub
13 min read
By Connor Mason on Nov 20, 2025 2:00:00 PM
In the ever-growing digital landscape of manufacturing operations, single use solutions & applications may solve issues, but also create their own data silos. These silos present multiple challenges (limited visibility, slower decision-making, security blind spots) and lead to missed opportunities due to the complex management of varying solutions. For example, OPC HDA is a standard utilized for collecting and sharing historical data across industrial automation technology solutions. Based on the standards of OPC DA, integration challenges arise due to the dependency of COM and remote DCOM connections, creating incompatibility with newer solutions and technologies.
Today we'll explore how Cogent DataHub was used to solve many of these integration headaches and silos by providing a middleware platform for connectivity between a variety of protocols and technologies. With the latest major revision of Cogent DataHub V11, the ability to collect historical OPC HDA data is now possible with the addition of the OPC HDA Client capability.
Tutorial: Fortify Data Integrity by Adding Store and Forward to PI Historian Logging
6 min read
By Nicole Knox on Sep 4, 2025 2:00:00 PM
Welcome back to our blog! In our previous post, Protecting Historical Data Integrity Using Store & Forward, we walked through several architectures that leverage Cogent DataHub to securely historize data while minimizing the risk of data loss. Today, we will expand on this concept by putting it into practice.
Why It Matters
Even a brief connection outage can lead to gaps in historized data, compliance risks, and lost insights. Store and Forward ensures your data is continuously captured and preserved, buffering data during interruptions and forwarding seamlessly once connections recover, so your operations stay resilient and reliable.
Protecting Historical Data Integrity Using Store & Forward
8 min read
By Jessica Dillon on Jul 31, 2025 2:00:00 PM
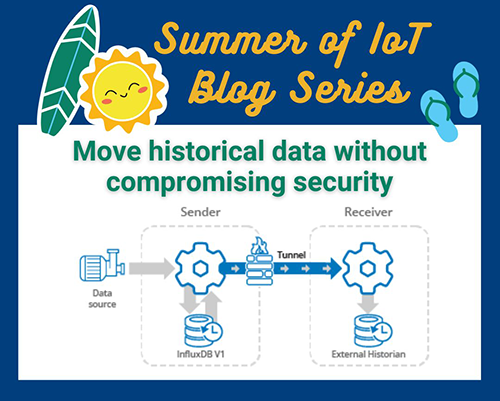
Welcome back to the Summer of IoT Blog Series. In this blog we’ll explore how Cogent DataHub’s External Historian and built-in Store and Forward features ensure efficient data flow without risking network security at the plant or enterprise level.
As organizations work toward Industry 4.0 and digital transformation, ensuring secure and reliable OT/IT convergence is essential for breaking down data silos and creating cohesion between your business systems. IoT devices provide real-time data and connectivity to transform traditional industrial operations. Complementing this, historians serve as centralized data repositories that store and organize time-series data from IoT devices and other sources. Together, the data from both fuels advanced analytics, automation, and smart decision-making across the enterprise.
UNS Without the Overhaul: Modernizing Industrial Data with Software Toolbox
4 min read
By Ryan Royse on Jul 17, 2025 2:00:00 PM
Welcome to the launch of Software Toolbox’s Summer of IoT blog series for 2025.
In the coming posts, we’ll explore how our solutions support the evolving world of the Industrial Internet of Things (IIoT), and more importantly, how they can help you advance your Industry 4.0 and digital transformation goals with practical, proven tools. We begin the series by exploring Unified Namespace (UNS), what it means, why it matters, and how Software Toolbox makes it practical for real-world industrial environments.
Unified Namespace, Real Results: Lessons and Tools that Deliver
In today’s fast-evolving industrial landscape, seamless connectivity and data integration are critical for operational success. At Software Toolbox, our solutions are designed to empower businesses by enabling UNS connectivity, bridging the gap between diverse systems and helping with efficiency, interoperability, and scalability.
Personally, as a presenter and attendee of ProveIt! 2025 and an attendee of 4.0 Solutions’ Edge Integration to UNS Workshop, I have had a lot of exposure to the topic of UNS this year. In this blog post, I will share not only what I have learned surrounding the topic, but how Software Toolbox’s solutions fit into the picture.
Video Tutorial: How to configure Cogent DataHub as an MQTT Broker
3 min read
By Connor Mason on May 8, 2025 2:00:00 PM
In the Industry 4.0 movement we are in today, companies going through the digital transformation process have to turn data into information and get it in the structures people want, how they want it and when they want it, to facilitate decisions that achieve the desired business results. Unifying data means accessing data where it lives, no matter the protocol required. MQTT is used extensively as a communication transport in many applications, and in this blog we'll show you an implementation.
Securing Oil and Gas Data Exchange with Software Toolbox Solutions
6 min read
By Jay David on May 1, 2025 2:00:00 PM
In the oil and gas industry, data drives everything—from production optimization to regulatory compliance and remote asset management. But in an environment with geographically dispersed assets, legacy equipment, and too often limited network bandwidth, secure data exchange is far from simple.
To stay competitive and compliant, oil and gas operators must bridge the gap between edge devices to control and enterprise systems—safely, reliably, and in real time.
How Remote Configuration Can Help Your Business Go Green
6 min read
By Zachary Parham on Apr 17, 2025 2:00:00 PM
While security and ease of project execution are often the focus when discussing remote configuration, they’re just the beginning. In this post for our 2025 Environmental Sustainability blog series, we’re highlighting the environmental benefits as well. Embracing remote configuration not only helps reduce emissions—it also enhances efficiency, sparks innovation, and supports long-term resilience for your business and the planet.
One of the most valuable lessons from the COVID-19 pandemic is that remote work can significantly reduce a company’s carbon emissions and overall environmental footprint. While individuals often concentrate on minimizing their direct emissions, businesses have the potential to drive far greater impact by addressing emissions at scale. True corporate sustainability requires a holistic approach—one that considers the full lifecycle of every product, process, and operation. Software Toolbox offers several secure remote configuration options to help you achieve sustainability goals—featuring solutions like OPC Server Remote Configuration Client, Cogent DataHub, and OPC Router.
About this Blog
We're engineers like you, so this blog focuses on "How to" appnotes, videos, tech team tips, product update announcements, user case studies, and other technical updates. Subscribe to updates below. Your feedback and questions on posts are always welcomed.
Subscribe to our Blog
Recent Posts
Posts by Topic
- Device Connectivity (205)
- Wonderware (178)
- OPC UA (121)
- Cogent DataHub (111)
- TOP Server (108)
- OPC (103)
- Technical Support (99)
- OmniServer (73)
- Video Tutorials (69)
- OPC Router (52)
- OPC DA (42)
- Protocols (40)
- AVEVA (37)
- Automation 101 (28)
- Security (26)
- MQTT & IoT (24)
- OmniServer Did You Know (24)
- Data Tunneling (23)
- Connectivity (22)
- OPC Data Client (22)
- Development Tools (19)
- IT/OT (19)
- DCOM (17)
- LGH (14)
- OPC Tunnel (13)
- Alarms & Notifications (12)
- Database (12)
- Earth Day (12)
- Summer of IoT (12)
- Exploring OPC UA (11)
- OPC Gateway (11)
- REST & Web Services (11)
- Case Studies (10)
- Dream Report (10)
- EFM (10)
- Oil & Gas (10)
- Reporting (10)
- CSV (9)
- Database & Historian (9)
- OPC Integration (9)
- Flow (8)
- OPC Server (8)
- Redundancy (8)
- Sustainability (8)
- AVEVA OPC UA Client (7)
- Modbus (7)
- OPC Router Basic Training (7)
- SuiteLink (7)
- DataHub Training (6)
- ODBC (6)
- OPC Alarms and Events (6)
- OPC Conversion (6)
- OPC Data Logger (6)
- ProtocolDesign (6)
- xml (6)
- Data Bridging (5)
- Data Logging (5)
- Data Storage Deep Dive (5)
- Business Intelligence (4)
- Data Integration (4)
- InTouch (4)
- Industrial Decisions (4)
- Industry 4.0 (4)
- OPC Bridge (4)
- OPC Redundancy (4)
- OPC Toolkit Benefits (4)
- OmniServer User Stories (4)
- SLIK-DA (4)
- SQL (4)
- Collaboration (3)
- Error Detection (3)
- IT & Infrastructure (3)
- OPC Server Remote Config (3)
- Wedges (3)
- Windows (3)
- ControlLogix (2)
- Excel (2)
- Ignition (2)
- KEPServerEX (2)
- Kepware Edge (2)
- OPC Wizard (2)
- OSIsoft (2)
- Omron (2)
- PGAS (2)
- Predictive Maintenance (2)
- Process Alert (2)
- Scripting (2)
- Store and Forward (2)
- System Integrators (2)
- Building Automation (1)
- ERP (1)
- Industrial AI (1)
- LGH User Stories (1)
- LRC (1)
- Linux (1)
- Machine Learning (1)
- Mining/Metals (1)
- New Release (1)
- Omni Flow (1)
- Power & Utilities (1)
- Predictive Analytics (1)
- Process Alerts (1)
- QNX (1)
- Sparkplug B (1)
- Water & Wastewater (1)