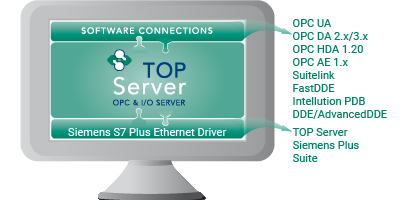
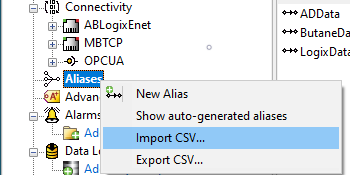
In keeping with ongoing continuous improvement initiatives, TOP Server for AVEVA V6.11 adds drivers, as well as enhancing existing drivers and resolving known issues for over 30 drivers and plug-ins.
In this post, we'll cover the key features released in V6.11 in more detail, namely the new Siemens S7 Plus Ethernet driver with symbolic address support for S7-1500 and S7-1200 controllers, several powerful scalability enhancements for BACnet and important updates to several oil and gas drivers, including how they benefit you as a TOP Server user.